This article is a part 3/3 of a series describing how to setup an Ephemeral Firefox session as a Site-Specific Browser. The ultimate goal is to be able to have a self-destructing browsing session that can only access a single company’s services, such as Google or Facebook.

- Part 1/3: Ephemeral Firefox in Ubuntu
- Part 2/3: Ephemeral Firefox with Extensions
- Part 3/3: Ephemeral Firefox as a Site-Specific Browser
After setting up the Site-Specific Ephemeral Firefox Browser, you can then blacklist services designated to your Site-Specific browser(s) (such as Google or Facebook) from your main browser. This significantly improves your ability to browse the internet without your activity being tracked by these companies — leaving your sensitive data vulnerable to being stolen by hackers.
EDIT 2019-03-30: A much simpler (and much less effective) solution to creating a facebook-specific browser would be to use Facebook Container in Firefox. This addon uses the container functionality in Firefox and automatically associates all requests to facebook websites into an isolated facebook-specific container. Source
Prereqs
Before proceeding, you must first execute the following prerequsites, which are detailed in my first and second posts on setting up an Ephemeral Firefox.
SKEL_PATH="$HOME/.mozilla/firefox/ephemeralFirefoxSkel"
sudo apt-get -y install firejail secure-delete
sudo firecfg --clean
# create skeleton directory for extensions, if necessary
[ ! -d "${SKEL_PATH}/extensions" ] && mkdir -p "${SKEL_PATH}/extensions"
# the name of the extensions found in this list must match the unique "slug" id
# of the extension as found in the URL. For example:
# * https://addons.mozilla.org/en-US/firefox/addon/https-everywhere/
extensions="https-everywhere ublock-origin cookie-autodelete privacy-badger17 chameleon-ext decentraleyes"
# for every extension, download it and rename it. For more info, see:
# * https://developer.mozilla.org/en-US/docs/Mozilla/Add-ons/WebExtensions/Distribution_options/Sideloading_add-ons
cd "${SKEL_PATH}/extensions"
for slug in $extensions; do
# download the file
downloadFileName="addon-${slug}-latest.xpi"
wget "https://addons.mozilla.org/firefox/downloads/latest/${slug}/${downloadFileName}"
# rename the file; the required new name is found in the manifest.json file
unzip -o "${downloadFileName}" manifest.json
newFileName="`cat manifest.json | python -c "import sys, json; print json.load(sys.stdin)['applications']['gecko']['id']"`.xpi"
rm manifest.json
mv "${downloadFileName}" "${newFileName}"
done
# allow extensions to be installed without human confirmation for faster startup
cat > "${SKEL_PATH}/user.js" <<'EOF'
user_pref("extensions.autoDisableScopes", 0);
EOF
Ephemeral Firefox Script
Copy the following script into '$HOME/bin/ephemeralFirefox.sh', make it executable, and make sure '$HOME/bin' is in your $PATH
Note the changes to the firejail from my previous posts. We add the --netfilter argument and the following necessary --dns arguments.
[ ! -d $HOME/bin/ ] && mkdir $HOME/bin
cat > $HOME/bin/ephemeralFirefox.sh <<'EOF'
#!/bin/bash
################################################################################
# Author: Michael Altfield <michael@michaelaltfield.net>
# Created: 2019-03-03
# Updated: 2019-03-25
# Version: 0.3
# Purpose: Start an Ephemeral Firefox with netfilter to make it Site-Specific
################################################################################
############
# SETTINGS #
############
INTERFACE="eth0"
TMP_PATH="$HOME/tmp/ephemeralFirefox"
SKEL_PATH="$HOME/.mozilla/firefox/ephemeralFirefoxSkel"
###############################
# CLEANUP OLD ORPHAN TMP DATA #
###############################
# loop through all the Ephemeral Firefox temp dirs
for tmpDir in $(find "${TMP_PATH}" -mindepth 1 -maxdepth 1 -type d); do
# is this temp dir for an Ephemeral Firefox that's still running? Or is it no longer needed?
if [[ -z `firejail --list | grep "${tmpDir}"` ]]; then
# this temp dir is no longer needed; delete it
echo "INFO: shredding data from old Ephemeral Firefox temp dir = ${tmpDir}"
srm -rfll "${tmpDir}"
fi
done
###################
# CREATE TEMP DIR #
###################
# first create a temp dir in our (hopefully encrypted) $HOME dir, if first run
[ ! -d "${TMP_PATH}" ] && mkdir -p "${TMP_PATH}"
# create temp dir for ephemeral session
tmpDir=`/bin/mktemp -p "$TMP_PATH" -d`
tmpProfileDir="${tmpDir}/firefoxProfile"
mkdir -p "${tmpProfileDir}"
echo "INFO: created Ephemeral Firefox temp profile dir = ${tmpProfileDir}"
###########################
# START EPHEMERAL FIREFOX #
###########################
# what should the homepage be?
url="${1}"
if [[ -z ${url} ]]; then
url="https://start.duckduckgo.com"
fi
# should we use a netfilter (for a site-specific browser config)?
netfilterFilePath="${2}"
if [[ -z "${netfilterFilePath}" ]]; then
firejailNetArgs="--net=${INTERFACE} --netfilter=/etc/firejail/ephemeralFirefox.net"
else
firejailNetArgs="--net=${INTERFACE} --netfilter=${netfilterFilePath}"
fi
# prepare extensions
cp -r "${SKEL_PATH}/extensions" "${tmpProfileDir}/extensions"
cp -r "${SKEL_PATH}/browser-extension-data" ${tmpProfileDir}/
cp "${SKEL_PATH}/user.js" "${tmpProfileDir}/"
cp "${SKEL_PATH}/extensions.json" "${tmpProfileDir}/"
# try disabling 'seccomp' if you encounter issues
#firejail --ignore=seccomp --whitelist="${tmpProfileDir}" --dns="1.1.1.1" --dns="9.9.9.9" --dns="8.8.8.8" ${firejailNetArgs} firefox -no-remote -new-instance -profile "${tmpProfileDir}" "${url}"
firejail --whitelist="${tmpProfileDir}" --dns="1.1.1.1" --dns="9.9.9.9" --dns="8.8.8.8" ${firejailNetArgs} firefox -no-remote -new-instance -profile "${tmpProfileDir}" "${url}"
###########
# CLEANUP #
###########
# fast (secure enough) wipe of tmp dir
srm -vrfll "${tmpDir}"
# clean exit
exit 0
EOF
chmod +x $HOME/bin/ephemeralFirefox.sh
PATH=$PATH:$HOME/bin
Ephemeral Firefox Desktop Shortcut
Now we create an xdg desktop entry and create a symlink to it for a shortcut on the desktop.
[ ! -d $HOME/.local/share/ ] && mkdir $HOME/.local/share/ cat << EOF > $HOME/.local/share/ephemeralFirefox.desktop [Desktop Entry] Type=Application Name=Ephemeral Firefox Icon=firefox Exec="$HOME/bin/ephemeralFirefox.sh" EOF ln -s $HOME/.local/share/ephemeralFirefox.desktop $HOME/Desktop/ chmod +x $HOME/Desktop/ephemeralFirefox.desktop
Facebook-Specific Ephemeral Browser
In this section we will setup a Facebook-Specific Ephemeral Browser
Facebook-Specific netfilter rules
To establish a Facebook-Specific browser, we utilize the --netfilter argument in firejail to specify a set of firewall rules that restrict the network access granted to firefox such that firefox can only send requests to ip addresses owned by Facebook, Inc.
Rather than limit the by domain names, I prefer to limit by the ip netblocks assigned to the Autonomous System (AS) number for Facebook, Inc = AS32934
We can get the list of facebook’s ip netblocks using whois, for example:
root@disp355:/home/user# whois -h whois.radb.net -- \ root@disp355:/home/user# '-i origin AS32934'| grep -e "^route:" ... route: 69.63.176.0/20 route: 66.220.144.0/20 route: 66.220.144.0/21 route: 69.63.184.0/21 route: 69.63.176.0/21 route: 74.119.76.0/22 route: 69.171.255.0/24 route: 173.252.64.0/18 route: 69.171.224.0/19 route: 69.171.224.0/20 root@disp355:/home/user#
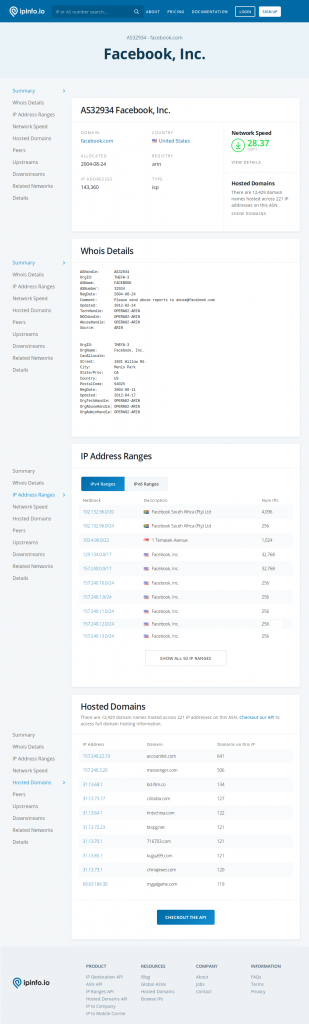
Or we can also check https://ipinfo.io/AS32934 (see screenshot to the right).
The resulting firewall rules [a] whitelist all the ipv4 netblocks owned by facebook, [b] whitelist outgoing dns queries, and block any other outgoing network traffic.
For incoming traffic we [a] whitelist dns traffic, [b] whitelist established connections, and block any other incoming network traffic.
sudo bash -c 'cat << EOF > /etc/firejail/facebookOnly.net ################################################################################ # Author: Michael Altfield <michael@michaelaltfield.net> # Created: 2019-03-25 # Updated: 2019-03-25 # Version: 0.1 # Purpose: Permits traffic to/from facebook (and dns) only ################################################################################ *filter :INPUT DROP [0:0] :FORWARD DROP [0:0] :OUTPUT DROP [0:0] -A OUTPUT --destination 102.132.96.0/20 -j ACCEPT -A OUTPUT --destination 102.132.96.0/24 -j ACCEPT -A OUTPUT --destination 103.4.96.0/22 -j ACCEPT -A OUTPUT --destination 129.134.0.0/17 -j ACCEPT -A OUTPUT --destination 157.240.0.0/17 -j ACCEPT -A OUTPUT --destination 157.240.10.0/24 -j ACCEPT -A OUTPUT --destination 157.240.1.0/24 -j ACCEPT -A OUTPUT --destination 157.240.11.0/24 -j ACCEPT -A OUTPUT --destination 157.240.12.0/24 -j ACCEPT -A OUTPUT --destination 157.240.13.0/24 -j ACCEPT -A OUTPUT --destination 157.240.14.0/24 -j ACCEPT -A OUTPUT --destination 157.240.15.0/24 -j ACCEPT -A OUTPUT --destination 157.240.18.0/24 -j ACCEPT -A OUTPUT --destination 157.240.19.0/24 -j ACCEPT -A OUTPUT --destination 157.240.192.0/18 -j ACCEPT -A OUTPUT --destination 157.240.193.0/24 -j ACCEPT -A OUTPUT --destination 157.240.194.0/24 -j ACCEPT -A OUTPUT --destination 157.240.195.0/24 -j ACCEPT -A OUTPUT --destination 157.240.20.0/24 -j ACCEPT -A OUTPUT --destination 157.240.2.0/24 -j ACCEPT -A OUTPUT --destination 157.240.21.0/24 -j ACCEPT -A OUTPUT --destination 157.240.22.0/24 -j ACCEPT -A OUTPUT --destination 157.240.24.0/24 -j ACCEPT -A OUTPUT --destination 157.240.25.0/24 -j ACCEPT -A OUTPUT --destination 157.240.26.0/24 -j ACCEPT -A OUTPUT --destination 157.240.27.0/24 -j ACCEPT -A OUTPUT --destination 157.240.28.0/24 -j ACCEPT -A OUTPUT --destination 157.240.29.0/24 -j ACCEPT -A OUTPUT --destination 157.240.30.0/24 -j ACCEPT -A OUTPUT --destination 157.240.3.0/24 -j ACCEPT -A OUTPUT --destination 157.240.6.0/24 -j ACCEPT -A OUTPUT --destination 157.240.7.0/24 -j ACCEPT -A OUTPUT --destination 157.240.8.0/24 -j ACCEPT -A OUTPUT --destination 157.240.9.0/24 -j ACCEPT -A OUTPUT --destination 173.252.64.0/19 -j ACCEPT -A OUTPUT --destination 173.252.88.0/21 -j ACCEPT -A OUTPUT --destination 173.252.96.0/19 -j ACCEPT -A OUTPUT --destination 179.60.192.0/22 -j ACCEPT -A OUTPUT --destination 179.60.192.0/24 -j ACCEPT -A OUTPUT --destination 179.60.193.0/24 -j ACCEPT -A OUTPUT --destination 179.60.194.0/24 -j ACCEPT -A OUTPUT --destination 179.60.195.0/24 -j ACCEPT -A OUTPUT --destination 185.60.216.0/22 -j ACCEPT -A OUTPUT --destination 185.60.216.0/24 -j ACCEPT -A OUTPUT --destination 185.60.217.0/24 -j ACCEPT -A OUTPUT --destination 185.60.218.0/24 -j ACCEPT -A OUTPUT --destination 185.60.219.0/24 -j ACCEPT -A OUTPUT --destination 204.15.20.0/22 -j ACCEPT -A OUTPUT --destination 31.13.24.0/21 -j ACCEPT -A OUTPUT --destination 31.13.64.0/18 -j ACCEPT -A OUTPUT --destination 31.13.64.0/19 -j ACCEPT -A OUTPUT --destination 31.13.64.0/24 -j ACCEPT -A OUTPUT --destination 31.13.65.0/24 -j ACCEPT -A OUTPUT --destination 31.13.66.0/24 -j ACCEPT -A OUTPUT --destination 31.13.67.0/24 -j ACCEPT -A OUTPUT --destination 31.13.68.0/24 -j ACCEPT -A OUTPUT --destination 31.13.70.0/24 -j ACCEPT -A OUTPUT --destination 31.13.71.0/24 -j ACCEPT -A OUTPUT --destination 31.13.72.0/24 -j ACCEPT -A OUTPUT --destination 31.13.73.0/24 -j ACCEPT -A OUTPUT --destination 31.13.74.0/24 -j ACCEPT -A OUTPUT --destination 31.13.75.0/24 -j ACCEPT -A OUTPUT --destination 31.13.80.0/24 -j ACCEPT -A OUTPUT --destination 31.13.81.0/24 -j ACCEPT -A OUTPUT --destination 31.13.82.0/24 -j ACCEPT -A OUTPUT --destination 31.13.83.0/24 -j ACCEPT -A OUTPUT --destination 31.13.84.0/24 -j ACCEPT -A OUTPUT --destination 31.13.85.0/24 -j ACCEPT -A OUTPUT --destination 31.13.86.0/24 -j ACCEPT -A OUTPUT --destination 31.13.87.0/24 -j ACCEPT -A OUTPUT --destination 31.13.89.0/24 -j ACCEPT -A OUTPUT --destination 31.13.90.0/24 -j ACCEPT -A OUTPUT --destination 31.13.91.0/24 -j ACCEPT -A OUTPUT --destination 31.13.92.0/24 -j ACCEPT -A OUTPUT --destination 31.13.93.0/24 -j ACCEPT -A OUTPUT --destination 31.13.94.0/24 -j ACCEPT -A OUTPUT --destination 31.13.95.0/24 -j ACCEPT -A OUTPUT --destination 31.13.96.0/19 -j ACCEPT -A OUTPUT --destination 45.64.40.0/22 -j ACCEPT -A OUTPUT --destination 66.220.144.0/20 -j ACCEPT -A OUTPUT --destination 66.220.144.0/21 -j ACCEPT -A OUTPUT --destination 66.220.152.0/21 -j ACCEPT -A OUTPUT --destination 69.171.224.0/19 -j ACCEPT -A OUTPUT --destination 69.171.224.0/20 -j ACCEPT -A OUTPUT --destination 69.171.239.0/24 -j ACCEPT -A OUTPUT --destination 69.171.240.0/20 -j ACCEPT -A OUTPUT --destination 69.171.250.0/24 -j ACCEPT -A OUTPUT --destination 69.171.255.0/24 -j ACCEPT -A OUTPUT --destination 69.63.176.0/20 -j ACCEPT -A OUTPUT --destination 69.63.176.0/21 -j ACCEPT -A OUTPUT --destination 69.63.184.0/21 -j ACCEPT -A OUTPUT --destination 74.119.76.0/22 -j ACCEPT -A OUTPUT -p udp --dport 53 -j ACCEPT -A OUTPUT -j DROP -A INPUT -p udp --sport 53 -j ACCEPT -A INPUT -m state --state ESTABLISHED -j ACCEPT -A INPUT -j DROP COMMIT EOF'
Ephemeral Firefox netfilter rules
Now that we have a netfilter ruleset that blocks everything except facebook (for the Ephemeral Facebook browser), let’s create a netfilter ruleset that allows everything except facebook (for the general Ephemeral Firefox browser).
sudo bash -c 'cat << EOF > /etc/firejail/ephemeralFirefox.net ################################################################################ # Author: Michael Altfield <michael@michaelaltfield.net> # Created: 2019-03-25 # Updated: 2019-03-25 # Version: 0.1 # Purpose: Permits traffic to/from everything except facebook ################################################################################ *filter :INPUT DROP [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [0:0] -A OUTPUT --destination 102.132.96.0/20 -j DROP -A OUTPUT --destination 102.132.96.0/24 -j DROP -A OUTPUT --destination 103.4.96.0/22 -j DROP -A OUTPUT --destination 129.134.0.0/17 -j DROP -A OUTPUT --destination 157.240.0.0/17 -j DROP -A OUTPUT --destination 157.240.10.0/24 -j DROP -A OUTPUT --destination 157.240.1.0/24 -j DROP -A OUTPUT --destination 157.240.11.0/24 -j DROP -A OUTPUT --destination 157.240.12.0/24 -j DROP -A OUTPUT --destination 157.240.13.0/24 -j DROP -A OUTPUT --destination 157.240.14.0/24 -j DROP -A OUTPUT --destination 157.240.15.0/24 -j DROP -A OUTPUT --destination 157.240.18.0/24 -j DROP -A OUTPUT --destination 157.240.19.0/24 -j DROP -A OUTPUT --destination 157.240.192.0/18 -j DROP -A OUTPUT --destination 157.240.193.0/24 -j DROP -A OUTPUT --destination 157.240.194.0/24 -j DROP -A OUTPUT --destination 157.240.195.0/24 -j DROP -A OUTPUT --destination 157.240.20.0/24 -j DROP -A OUTPUT --destination 157.240.2.0/24 -j DROP -A OUTPUT --destination 157.240.21.0/24 -j DROP -A OUTPUT --destination 157.240.22.0/24 -j DROP -A OUTPUT --destination 157.240.24.0/24 -j DROP -A OUTPUT --destination 157.240.25.0/24 -j DROP -A OUTPUT --destination 157.240.26.0/24 -j DROP -A OUTPUT --destination 157.240.27.0/24 -j DROP -A OUTPUT --destination 157.240.28.0/24 -j DROP -A OUTPUT --destination 157.240.29.0/24 -j DROP -A OUTPUT --destination 157.240.30.0/24 -j DROP -A OUTPUT --destination 157.240.3.0/24 -j DROP -A OUTPUT --destination 157.240.6.0/24 -j DROP -A OUTPUT --destination 157.240.7.0/24 -j DROP -A OUTPUT --destination 157.240.8.0/24 -j DROP -A OUTPUT --destination 157.240.9.0/24 -j DROP -A OUTPUT --destination 173.252.64.0/19 -j DROP -A OUTPUT --destination 173.252.88.0/21 -j DROP -A OUTPUT --destination 173.252.96.0/19 -j DROP -A OUTPUT --destination 179.60.192.0/22 -j DROP -A OUTPUT --destination 179.60.192.0/24 -j DROP -A OUTPUT --destination 179.60.193.0/24 -j DROP -A OUTPUT --destination 179.60.194.0/24 -j DROP -A OUTPUT --destination 179.60.195.0/24 -j DROP -A OUTPUT --destination 185.60.216.0/22 -j DROP -A OUTPUT --destination 185.60.216.0/24 -j DROP -A OUTPUT --destination 185.60.217.0/24 -j DROP -A OUTPUT --destination 185.60.218.0/24 -j DROP -A OUTPUT --destination 185.60.219.0/24 -j DROP -A OUTPUT --destination 204.15.20.0/22 -j DROP -A OUTPUT --destination 31.13.24.0/21 -j DROP -A OUTPUT --destination 31.13.64.0/18 -j DROP -A OUTPUT --destination 31.13.64.0/19 -j DROP -A OUTPUT --destination 31.13.64.0/24 -j DROP -A OUTPUT --destination 31.13.65.0/24 -j DROP -A OUTPUT --destination 31.13.66.0/24 -j DROP -A OUTPUT --destination 31.13.67.0/24 -j DROP -A OUTPUT --destination 31.13.68.0/24 -j DROP -A OUTPUT --destination 31.13.70.0/24 -j DROP -A OUTPUT --destination 31.13.71.0/24 -j DROP -A OUTPUT --destination 31.13.72.0/24 -j DROP -A OUTPUT --destination 31.13.73.0/24 -j DROP -A OUTPUT --destination 31.13.74.0/24 -j DROP -A OUTPUT --destination 31.13.75.0/24 -j DROP -A OUTPUT --destination 31.13.80.0/24 -j DROP -A OUTPUT --destination 31.13.81.0/24 -j DROP -A OUTPUT --destination 31.13.82.0/24 -j DROP -A OUTPUT --destination 31.13.83.0/24 -j DROP -A OUTPUT --destination 31.13.84.0/24 -j DROP -A OUTPUT --destination 31.13.85.0/24 -j DROP -A OUTPUT --destination 31.13.86.0/24 -j DROP -A OUTPUT --destination 31.13.87.0/24 -j DROP -A OUTPUT --destination 31.13.89.0/24 -j DROP -A OUTPUT --destination 31.13.90.0/24 -j DROP -A OUTPUT --destination 31.13.91.0/24 -j DROP -A OUTPUT --destination 31.13.92.0/24 -j DROP -A OUTPUT --destination 31.13.93.0/24 -j DROP -A OUTPUT --destination 31.13.94.0/24 -j DROP -A OUTPUT --destination 31.13.95.0/24 -j DROP -A OUTPUT --destination 31.13.96.0/19 -j DROP -A OUTPUT --destination 45.64.40.0/22 -j DROP -A OUTPUT --destination 66.220.144.0/20 -j DROP -A OUTPUT --destination 66.220.144.0/21 -j DROP -A OUTPUT --destination 66.220.152.0/21 -j DROP -A OUTPUT --destination 69.171.224.0/19 -j DROP -A OUTPUT --destination 69.171.224.0/20 -j DROP -A OUTPUT --destination 69.171.239.0/24 -j DROP -A OUTPUT --destination 69.171.240.0/20 -j DROP -A OUTPUT --destination 69.171.250.0/24 -j DROP -A OUTPUT --destination 69.171.255.0/24 -j DROP -A OUTPUT --destination 69.63.176.0/20 -j DROP -A OUTPUT --destination 69.63.176.0/21 -j DROP -A OUTPUT --destination 69.63.184.0/21 -j DROP -A OUTPUT --destination 74.119.76.0/22 -j DROP -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT -A INPUT -j DROP COMMIT EOF'
Facebook-specific Ephemeral Firefox script
And now we create a simple wrapper script for the ephemeralFirefox.sh script called ephemeralFacebook.sh. This will make the Ephemeral Firefox firejail [a] use the netfilter created above to only permit traffic to/from Facebook-owned ip netblocks and [b] open the browser at facebook.com
[ ! -d $HOME/bin/ ] && mkdir $HOME/bin cat > $HOME/bin/ephemeralFacebook.sh <<'EOF' #!/bin/bash ################################################################################ # Author: Michael Altfield <michael@michaelaltfield.net> # Created: 2019-03-25 # Updated: 2019-03-25 # Version: 0.1 # Purpose: Wrapper script to execute Facebook-Specific Ephemeral Firefox ################################################################################ $HOME/bin/ephemeralFirefox.sh "https://www.facebook.com" "/etc/firejail/facebookOnly.net" # clean exit exit 0 EOF chmod +x $HOME/bin/ephemeralFacebook.sh PATH=$PATH:$HOME/bin
Facebook-Specific Browser Shortcut
Finally, we create another xdg desktop entry for the Facebook-Specific Ephemeral Browser and create a shortcut on the desktop.
[ ! -d $HOME/.local/share/ ] && mkdir $HOME/.local/share/ [ ! -d $HOME/.local/share/icons ] && mkdir $HOME/.local/share/icons wget -O $HOME/.local/share/icons/facebook.png https://facebook.com/apple-touch-icon.png cat << EOF > $HOME/.local/share/ephemeralFacebook.desktop [Desktop Entry] Type=Application Name=Ephemeral Facebook Icon=$HOME/.local/share/icons/facebook.png Exec="$HOME/bin/ephemeralFacebook.sh" EOF ln -s $HOME/.local/share/ephemeralFacebook.desktop $HOME/Desktop/ chmod +x $HOME/Desktop/ephemeralFacebook.desktop
Conclusion
You now should now have two shortcuts on your desktop.
The desktop shortcut that shows the facebook logo will open a Facebook-specific Ephemeral Firefox session such that it is locked in a firejail with firewall rules that only permit it to access servers owned by Facebook, Inc. When this browser is closed, all data on your computer associated with your browsing session will be securely deleted/wiped/shredded by srm.
The desktop shortcut that shows the firefox logo will open a general Ephemeral Firefox session such that it is also locked in a firejail with firewall rules that permit it to access all servers on the Internet except servers owned by Facebook, Inc. When the browser is closed, all data on your computer associated with your browsing session will be security deleted/wiped/shredded by srm.
This model could be further extended by creating Site-Specific Ephemeral Firefox scripts for other multinational corporations infamous for tracking and storing information about clients, such as Google.
Improvements
While the model described in this article significantly improves your privacy, there exists many potential improvements to further reduce tracking.
DNS
The Ephemeral Firefox session described in this article depends on DNS provided by Cloudflare, Quad9, or Google. The connection made to these services is not confidential (as could be provided by DNS over TLS) nor authenticated (as could be provided by DNSSEC)
An improvement would be to:
- run stubby (optionally with unbound) on the client,
- update the netfilter rules to allow dns queries only to 127.0.0.1, and
- change the firejail
--dnsargument’s value to 127.0.0.1
IPv6
For simplicity, the netfilter firewall rules used in this article only include IPv4 netblocks. To be more complete, it could/should include IPv6 addresses using the --netfilter6 argument for firejail.
3rd party hosting providers
Unfortunately, Facebook, Inc hosts some content on other company’s servers — whose IP addresses are not included in their ip namespace assigned by ARIN.
Indeed, Facebook, Inc. uses wordpress.com to host several of their websites. For example:
As such, these websites will not be blocked by the netfilter rules as described in this article.
Therefore, it may be wise to add additional rules to firefox to block facebook-owned domain names as well:
- *.facebook.com
- *.fbcdn.net
- *.fb.me
- *.fbsbx.com
- *.workplace.com
TAILS
Note that this Ephemeral Firefox solution does not (attempt to) achieve anonymity. While an Ephemeral Firefox session may help you avoid websites tracking your internet history via fingerprinting, there are other techniques that can be employed to track your activity other than fingerprinting. One obvious example is your geolocation, ISP, or IP Address. To further avoid tracking via these metrics, consider getting a VPN provider. After getting a VPN, consider setting-up a Whole House VPN.
Moreover, if you are an investigative journalist, activist, or political dissident looking to safely browse the internet without being tracked by an oppressive regime, this solution is not for you. If you’re concerned that an adversary having access to your Internet activity could cause pain, suffering, or loss-of-life, then you should not trust this system to protect you. Instead, you should use TAILS.
And if you like the idea of compartmentalization of your firefox activity into a Site-Specific Ephemeral Firefox, you may want to checkout QubesOS. Qubes is an entire OS designed with the principle of security through compartmentalization. Instead of merely creating a disposable Ephemeral Firefox, you can quickly & easily create a whole Disposable Virtual Machine.
Further Reading
This articles is part 3 of a 3-part series on Ephemeral Firefox. The other parts can be found here:
- Part 1/3: Ephemeral Firefox in Ubuntu
- Part 2/3: Ephemeral Firefox with Extensions
- Part 3/3: Ephemeral Firefox as a Site-Specific Browser
Related Posts
Hi, I’m Michael Altfield. I write articles about opsec, privacy, and devops ➡











Leave a Reply