This article will describe how to bypass censorship from within any network that uses firewalls using Deep Packet Inspection (DPI) built by the Israeli software company Check Point Software Technologies Ltd, such as is being used by the Miami-Dade’s Public Library System to censor on their public wifi.
I’ve been very fortunate to live in a country where freedom of speech is a well-protected human right and censorship is generally unaccepted. But, I’ve long been aware that many States prefer to assert their control over their citizens by controlling their available information. One of the shining achievements from the Tor Project is a system that allows these unfortunate souls to be able to bypass these censors and access the unfettered Internet. Indeed, the UN affirmed that a State’s attempt to prevent or disrupt dissemination of information online is a violation of international human rights law, as defined by article 19 of the Universal Declaration of Human Rights.
Of course, many States today continue to ban access to the Tor network. In response, Tor provided hidden entry-points called bridge relays that are harder to block. In response to Tor bridges, States purchased firewalls from companies like Check Point to analyze the behavior of traffic using a technique known as Deep Packet Inspection (DPI). And Tor responded by providing pluggable transports.
Enter Miami-Dade Public Library
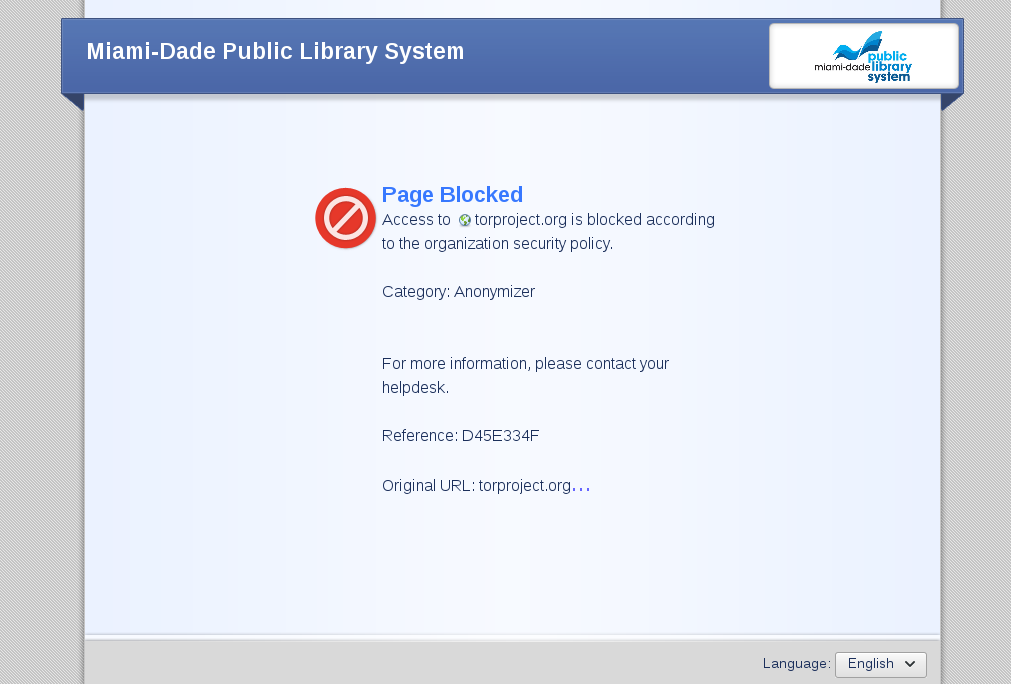
I was surprised when I stopped into a library today and discovered that I couldn’t connect to my VPN. I couldn’t get any work done, so I began to troubleshoot. I tested Tor; it was blocked. I went to ‘torproject.org’, and I got an interesting error from the Library’s firewall telling me that the site was banned because it fell under the category “Anonymizer”.
Page Blocked
Access to torproject.org is blocked according to the organization security policy.Category: Anonymizer
For more information, please contact your helpdesk.
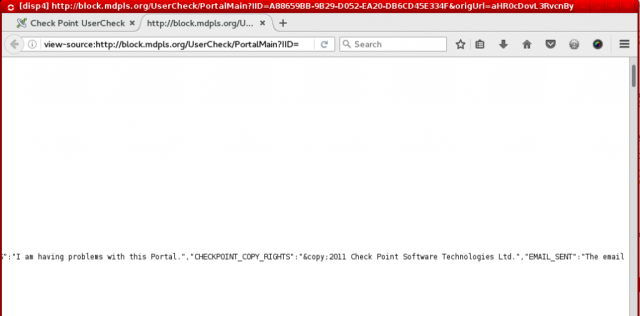
I checked the source code of the page giving me the error, and I soon discovered a copyright on behalf of “Check Point Software Technologies Ltd”. Further digging showed that this was an Israeli Security company that manufactures firewalls with DPI and the “function” to block potentially Anonymizing networks like VPNs and Tor.
Thus began my tinkering with Tor Bridges and pluggable transports.
Bypassing DPI
If you want to get around this DPI censor from a Check Point firewall, do as follows:
- Download the latest Tor Browser Bundle from torproject.org
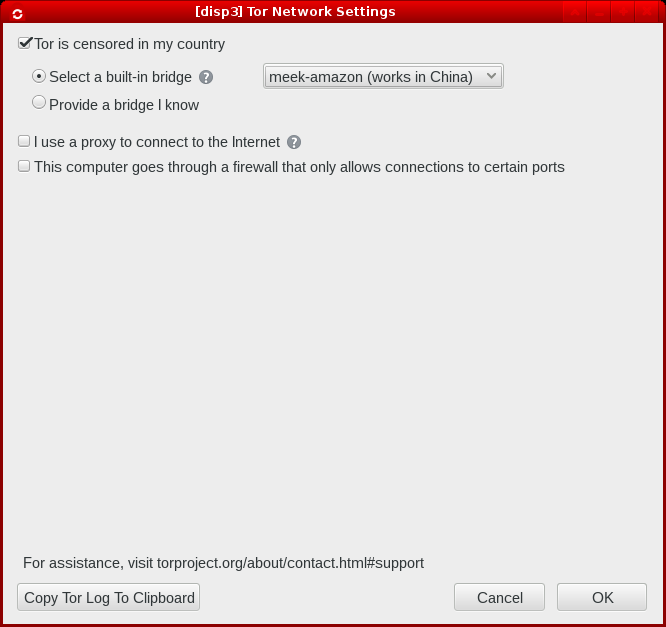
- When starting the Tor Browser Bundle for the first time, check the “Tor is censored in my country” checkbox
- Choose “Select a built-in bridge”
- In the drop-down, select “meek-amazon”
- Click OK
Note that if your firewall blocks access to
torproject.org, effectively preventing you from downloading the Tor Browser Bundle, you have other options to download Tor. You can, for example, get an out-of-band version of the download from the GetTor robot by emailinggettor@torproject.org or by sending a PM to twitter user @get_tor. In my case, the MDPL blockedhttp://torproject.org, but they didn’t blockhttps://torproject.org. shurg
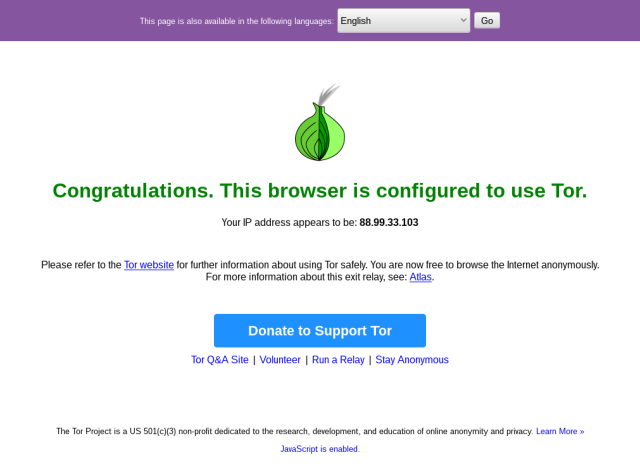
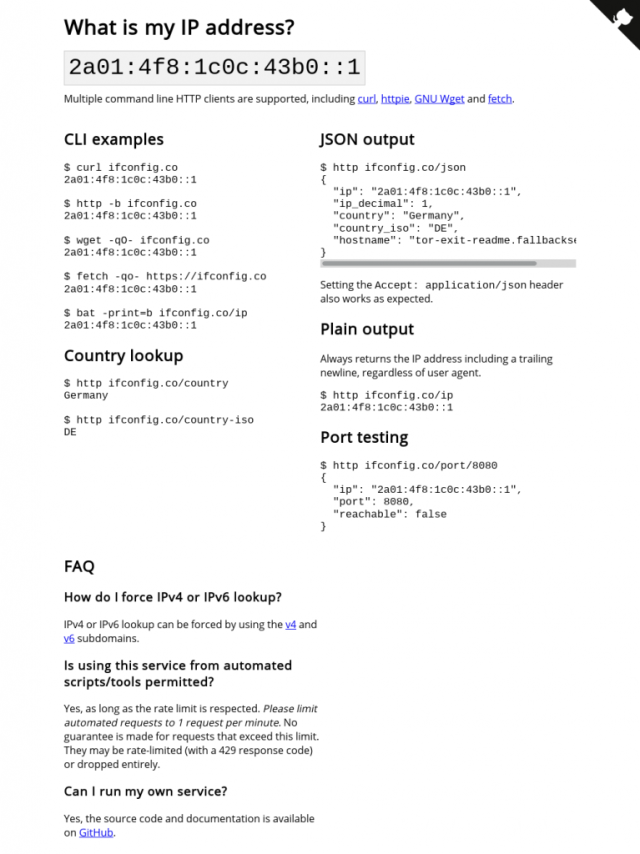
You should now be able to connect to Tor. When the Tor Browser opens, attempt to access the following 2 sites to check your Tor Connection:
1. check.torproject.org
2. ifconfig.co
Fronting
Unfortunately, I found that the obfs3, obfs4, and fte pluggable transports did not work on this network. The pluggable transport that did work was meek-amazon.
Meek uses a clever technique known as Domain Fronting. It leverages the TLS extension Server Name Indication (SNI)–which is traditionally used for servers hosting content for multiple domains over the same ip address and port–and popular CDNs that governments cannot afford to block wholesale. For example, meek-amazon encodes all of our outgoing packets with a destination pointed to a domain on the Amazon CloudFront CDN. The contents of the encrypted packets would include a “Host” header telling the CDN where to foward the packet–but only the client (us) and Amazon can read this encrypted header.
So the firewall merely sees that we’re talking with a server on the Amazon Cloud, and it passes our packet along. Amazon decrypts the packet, sees it has a Host header, and it passes it to the Tor relay.
For a detailed technical view of this technique, see the meek section of the Tor Project’s documentation page “A Child’s Garden Of Pluggable Transports”.
If for some reason meek-amazon doesn’t work for you, try substituting the front domain with another popular CDN–or just a different domain by the same company–as described in this tor-talk What do I do if meek gets blocked?.
Conclusion
As a side note, Check Point also markets their software for its ability to do what they call “SSL Inspection” That is to say, they provide an easy mechanism for a system administrator to issue a man-in-the-middle attack on a user on the network. It does so by generating a self-signed certificate and injecting it in place of the valid certificate. Thus defeating the whole purpose of https: privacy.
It’s one thing for security researchers to publish a proof-of-concept of a MITM attack to demonstrate the inherent weakness of the X.509 trust model. It’s something else to build this as a product, market it as a feature, and sell it to States. Indeed, Check Point is doing some nasty business that many would consider criminal.
Now I just need to test a stunnel’d openvpn connection using AirVPN to bypass this library’s VPN blocking so I can actually get some work done!
Limitations
Please note that this guide was written for people living in countries where it is legal to use anonymizing & censorship-defeating technology.
If you live in an oppressive regime where it is unlawful to attempt to use software like Tor, you should consider using TAILS instead of the Tor Browser Bundle.
Related Posts
Hi, I’m Michael Altfield. I write articles about opsec, privacy, and devops ➡









[…] Detect outgoing port blocking with nmap and portquiz.net Bypassing Check Point firewall DPI Tor-blocking […]